Network segmentation is emerging as a critical strategy as industrial companies connect their OT and IT networks. This tactic makes it possible to preserve the key features of industrial assets while effectively protecting them.
Network segmentation isn’t new. It has long been used to divide physical networks into sub-networks. The starting point is always a single physical network, which is divided logically using a software-defined networking (SDN) approach.
Dividing a network into subnetworks leads to increased speed and performance. Since traffic is largely limited to communication between devices within the subnetwork, there’s no unrelated traffic to cause congestion.
But segmentation also provides substantial security advantages. Each subnetwork is dedicated to activities that require specific functions and that can only be accessed by a predetermined group of employees. As a result, a company’s sales, customer service, accounting and human resources teams can access the servers and data they need to do their jobs, but they can’t access anything else. This helps keep data private, prevent leaks and stop unauthorized access.
If an intrusion or failure occurs, any damage is limited to the affected subnetwork. In short, segmentation is a simple way to contain attacks and incidents.
This is exactly the type of protection that industrial OT networks need.
Why opt for segmentation?
Compared with IT networks, OT networks tend to include a more diverse range of devices.
- It’s not unusual to have industrial tools, conveyors, sensors, temperature or pressure controllers, and more.
- Some of these devices are extremely expensive, costing much more than a computer server. Malfunction or misuse can cause serious damage and could even physically harm individuals in the vicinity.
- While most employees and managers know how to use a computer, only those with specialized training know how to operate production equipment.
These characteristics are why the OT network should be a separate subnetwork. It’s important to maintain its specific features while integrating it with the IT network.
Network segmentation is the easiest way to meet these two imperatives at the same time.
How to segment a network?
OT network segmentation is usually carried out in layers.
- The lowest layer is closest to the physical world and is directly concerned with production and capturing data about the production environment (temperature, pressure, location, speed, etc.).
- Additional layers rise progressively up to management level, the corporate network and the internet.
A typical OT network segmentation would include four superimposed layers (Layer 0 to Layer 3) within an industrial zone. Here’s a simplified diagram of what it might look like:
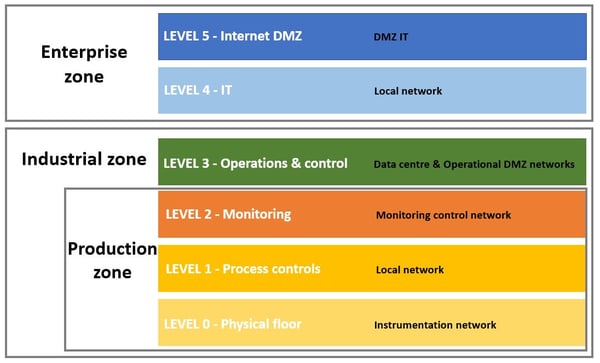
An industrial zone is usually specific to a physical industrial site, such as a manufacturing plant. It is located below the enterprise zone, which covers all the company’s sites, support functions (Finance, HR, Marketing and so on) and internet communications. The industrial zone covers the entire site’s operations management and the various networks for its production zones.
- A production zone (Levels 0 to 2) is a functional area within an industrial zone. For example, in an automobile manufacturing plant, it could be a bodywork shop or a sub-assembly process. In a food and beverage processing plant, it could be a batch mixing zone.
- The highest level of the industrial zone (Level 3) includes essential systems and equipment used for industrial operations monitoring and control. To keep the facilities, systems and network running properly, this zone needs clear and logical rules as well as a powerful security system.
In order for a company to be able to control the functional process, all networks must be able to communicate in real time and according to strict access protocols.
Here’s a detailed explanation of each level in an industrial zone:
Level 0: Physical floor
- Use: Basic functions of the industrial automation and control system, such as motor speed, measurement variables, output settings and the execution of critical functions (e.g., painting, welding, folding, etc.)
- Connected devices: Wide variety of sensors, actuators and devices involved in basic manufacturing processes
- Typical users: Operators
Level 1: Process control
- Use: Control industrial equipment
- Connected devices: Programmable logic controllers that activate or drive the motors, valves or switches used in industrial processes
- Typical users: Operators
Level 2: Monitoring (production management)
- Use: Organize and monitor production to optimize processes and ensure continuity
- Connected devices: Human-machine interface terminals, control-room workstations and alarm systems
- Typical users: Engineers or industrial foremen
Level 3: Operations and control
- Use: Industrial automation and control systems. The systems and applications at this level manage automation and industrial controls site-wide.
- Installed systems and features: Administration and control applications (e.g., domain servers, patch distribution, terminal services), equipment management, detailed production planning and production reporting (e.g., cycle times, quality index, predictive maintenance)
- Typical users: Engineers, industrial foremen and managers
Each level/layer has its own access protocols, but the rules for the lower levels are usually more numerous and more restrictive. The subnetworks in the lower levels are also restricted to fewer users.
There are also firewalls separating the subnetworks in different layers.
At a high level, this kind of segmentation makes it possible to filter traffic, data and applications by function type and user needs.
If necessary, levels can be sub-divided into homogeneous subnetworks. For example, a parts manufacturing process might have its own subnetwork, separate from the subnetwork for a parts assembly process. Segmentation separates the two, though they are both “supervised” by the level above them.
Software-defined segmentation can adapt the physical network to needs stemming from production processes.
Proper segmentation is critical for ensuring optimal converged IT/OT network performance, resilience and security.
Are you interested in updating your enterprise network to improve its performance, security and resilience? NOVIPRO can help. Our experts will analyze your current network configuration and recommend improvements to prepare you for Industry 4.0. Contact us and let us know the issues you’re facing.
Read the next article of our serie: Why network management systems make OT networks more secure?